为 Tableau Server 配置代理
- 版本 :2022.1 及更高版本
在大多数企业中,Tableau Server 需要与互联网进行通信。Tableau Server 被设计为在受保护的内部网络中运行。请勿直接在互联网上或 DMZ 中设置 Tableau Server。相反,您的网络和互联网之间的通信应该使用代理服务器进行调解。转发代理服务器将流量从网络内部调解到互联网上的目标。反向代理服务器将流量从互联网中介到网络内部的目标。
谁应该阅读这篇文章?
本文面向在常规网络和网关代理解决方案方面经验丰富的 IT 专业人员。本文介绍了 Tableau 如何以及何时需要访问 Internet,并介绍了如何配置您的网络和 Tableau 以使用正向和反向代理服务器来访问互联网。有许多可用的第三方代理解决方案,因此本文中的某些内容必然是通用的。
在配置代理服务器之前,请参阅与互联网通信。
配置转发代理服务器
要启用从 Tableau Server 到 Internet 的通信,请在转发代理服务器后面部署 Tableau Server。当 Tableau Server 需要访问互联网时,它不会将请求直接发送到互联网。相反,它将请求发送到转发代理,转发代理又转发请求。转发代理可帮助管理员管理发往 Internet 的流量,以执行负载平衡、阻止访问站点等任务。
如果使用转发代理,则必须将网络内运行 Tableau Server 的计算机配置为将流量发送到转发代理。Tableau Server 不支持直通或手动代理身份验证。
如果使用转发代理解决方案运行 OpenID 身份验证,则需要进行其他配置。请参阅配置 OpenID 以使用转发代理。
在 Windows 上配置 Tableau Server 以使用转发代理
在 Tableau Server 计算机上配置 Internet 选项的步骤取决于以下哪种方案描述了您的企业:
您的组织不使用转发代理解决方案。如果您的组织未运行代理解决方案,并且您安装 Tableau Server 的计算机可以与 Internet 通信,则无需执行此处的过程。
部署代理解决方案,并自动配置文件定义连接设置。如果您的组织使用自动配置文件(如 PAC 或文件)来指定 Internet 连接信息,则可以在 Windows 的“局域网 (LAN) 设置”对话框中使用此信息。有关详细信息,请参阅在 Microsoft 支持站点上启用浏览器设置的自动检测和配置。
.ins部署了代理解决方案,但未部署自动配置文件。对于此方案,您必须在运行 Tableau Server 的 Windows 计算机上配置 LAN 设置,以便在用户运行身份帐户的安全上下文中运行与代理服务器的连接。您还必须将其他内部 Tableau Server 实例配置为例外。
localhost
以下过程介绍了最后一个方案的步骤, 即没有自动配置文件的代理解决方案,其中 Tableau Server 在 Windows Server 上运行。
注: 如果您使用的是 Tableau Server 的分布式安装,请在初始服务器节点和每个附加节点上执行以下过程。
步骤 1:将运行身份服务帐户添加到本地管理员组
若要执行此过程,必须使用 作为运行身份服务帐户登录到 Tableau Server 计算机。默认情况下,“本地登录”策略不应用于运行身份服务帐户。因此,您必须临时将运行身份服务帐户添加到本地管理员组。
如果尚未在计算机上安装 Tableau Server,请参阅更改运行身份服务帐户。如果已安装 Tableau Server 并配置了运行身份服务帐户,则可以通过登录到 TSM Web UI 来确定运行身份服务帐户名称。Tableau 服务器运行身份服务帐户列在“配置”窗口的“安全”选项卡上。请参阅登录到 Tableau Services Manager Web UI。
使用 Microsoft 网站上将成员添加到本地组中的步骤,将运行身份服务帐户添加到本地管理员组。配置完转发代理信息后,将从“本地管理员”组中删除运行身份服务帐户。
步骤 2:在 Windows LAN 设置中配置代理服务器
使用运行身份服务帐户,登录到安装或将要安装 Tableau Server 的计算机。
打开“局域网 (LAN) 设置”对话框。(访问此对话框的一种快速方法是在 Windows 的“开始”菜单中进行搜索。在“Internet 属性”对话框中,单击“连接”选项卡,然后单击“LAN 设置”。
Internet Options在“代理服务器”下,选择“为 LAN 使用代理服务器”,输入代理服务器地址和端口,然后选择“对本地地址不使用代理服务器”。
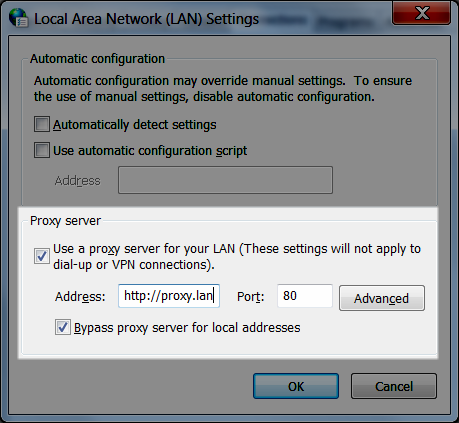
将此对话框保持打开状态,然后继续执行下一步。
步骤 3:添加例外以绕过代理服务器
您可以向此代理配置添加例外,以确保本地 Tableau Server 群集中的所有通信(如果您现在有一个或以后将有一个)都不会路由到代理服务器。
在“LAN 设置”对话框中,单击“高级”。(仅当您选择了为 LAN 使用代理服务器的选项时,此按钮才可用。
在“代理设置”对话框的“例外”字段中,输入以下内容:
使用分号分隔项目。
localhost同一群集中其他 Tableau Server 计算机的服务器主机名和 IP 地址。
关闭“代理设置”对话框和“局域网 (LAN) 设置”对话框。
在“Internet 属性”对话框中,单击“确定”以应用设置。
Stay logged onto the computer and continue to the next step.
Step 4: Verify proxy settings do not conflict with Windows environment variables
Some organizations configure forward proxy settings as environment variables in the Windows operating system. If such settings are configured on the computer that is running Tableau Server, then you must verify that they do not conflict with the configurations you've completed here.
On the computer that is running Tableau Server, enter "advanced system settings" in the search box and then click Enter to open the System Properties box.
On the Advanced tab, click Environment Variables.
Scroll through the System variables field.
If or are specified, verify that the values do not conflict with the proxy server address that you configured in the previous step.
http_proxyhttps_proxythe host name,
IP address, and
port of the Tableau Server for the value
If the existing settings do not conflict, then go to "Step 5: Test the proxy configuration."
If the existing settings do conflict, then create a new variable named , and enter:
no_proxyFor example, . For more information see the Microsoft MSDN article, Set Environment Variables.
localhost,192.168.0.10:80Click OK.
Step 5: Test the proxy configuration
To test the new configurations, while still logged in with the Run As service account on the Tableau Server computer, open a web browser and test the following Tableau URLs:
https://mapsconfig.tableau.com/v1/config.json and will prompt you to download a json file.https://api.mapbox.com/
Step 6: Remove the Run As service account from the Local Administrator group
After you have tested the proxy settings, remove the Run As service account from the Local Administrators group. Leaving the Run As service account in the administrator group elevates the permissions of the Run As service account and is a security risk.
Restart Tableau Server to ensure that all changes are implemented.
Server crash reporter
If your organization uses a proxy server to connect to the internet then you must configure Tableau Server's crash reporter to use the proxy. Even if you have already configured Tableau Server to use a proxy, you must also configure server crash reporter separately. To configure proxy for server crash reporter, see Configure Server Crash Reporter.
How a reverse proxy works with Tableau Server
A reverse proxy is a server that receives requests from external (internet) clients and forwards them to Tableau Server. Why use a reverse proxy? The basic answer is security. A reverse proxy makes Tableau Server available to the internet without having to expose the individual IP address of that particular Tableau Server to the internet. A reverse proxy also acts as an authentication and pass-through device, so that no data is stored where people outside the company can get to it. This requirement can be important for organizations that are subject to various privacy regulations such as PCI, HIPAA, or SOX.
The following diagram illustrates the communication path when a client makes a request to Tableau Server that is configured to work with a reverse proxy server.
An external client initiates a connection to Tableau Server. The client uses the public URL that's been configured for the reverse proxy server, such as . (The client doesn't know that it's accessing a reverse proxy.)
https://tableau.example.comThe reverse proxy maps that request in turn to a request to Tableau Server. The reverse proxy can be configured to authenticate the client (using SSL/TLS) as a precondition to passing the request to Tableau Server.
Tableau Server gets the request and sends its response to the reverse proxy.
The reverse proxy sends the content back to the client. As far as the client is concerned, it just had an interaction with Tableau Server, and has no way to know that the communication was mediated by the reverse proxy.
Proxy servers and SSL
For better security, you should configure reverse proxy servers to use SSL for any traffic that's external to your network. This helps to ensure privacy, content integrity, and authentication. Unless you've deployed other security measures to protect traffic between your internet gateway and Tableau Server, we also recommend configuring SSL between the gateway proxy and Tableau Server. You can use internal or self-signed certificates to encrypt traffic between Tableau Servers and other internal computers.
Mobile access
Tableau Server adds an X-header to all HTTP responses for Tableau Mobile sessions. By default, most proxy solutions will preserve X-headers. If your proxy solution does not preserve X-headers, then you will need to configure your proxy server to preserve the following header to all HTTP responses for Mobile client sessions: .X-Tableau: Tableau Server
If you have configured authentication at the proxy server gateway, then your proxy server must respond to Tableau Mobile HTTP requests with a HTTP 302 response. The 302 must include a redirect to the identity provider login page. To view a diagram that describes the 302 authentication sequence, see Tableau Mobile Authentication Sequence in the Tableau Community.
Reverse proxy and user authentication
Tableau Server will always authenticate users. This means that even if you are authenticating inbound connections at the gateway for your organization, Tableau Server will still authenticate the user.
However, not all clients will support user authentication with a reverse proxy:
For supported web browsers, you can use SAML, OpenID Connect, Kerberos, Trusted Tickets or manual authentication with a reverse proxy.
Tableau Mobile supports SAML or manual authentication with a reverse proxy. The iOS version of Tableau Mobile additionally supports Kerberos with a reverse proxy. The same recommendation above applies.
Tableau Prep does not support authentication with a reverse proxy. For remote access, use a VPN solution or configure your reverse proxy to route traffic from Tableau Prep directly to Tableau Server for authentication.
Tableau Desktop supports authentication with a reverse proxy provided that an authentication module is performing preauthentication on the reverse proxy before traffic is routed to Tableau Server for final authentication. For more information, see Part 5 - Configuring Web Tier of the Tableau Server Enterprise Deployment Guide and Configure Authentication Module with Independent Gateway.
If your organization is authenticating with Active Directory:
Active Directory with Enable automatic logon (SSPI) is not supported with a reverse proxy.
Tableau Server must be configured for reverse proxy before configuring Tableau Server for Kerberos. For more information, see Configure Kerberos.
Configure Tableau Server to work with a reverse proxy server
Before you configure Tableau Server, you'll need to collect the following information about the proxy server configuration. To configure Tableau Server, you use the command. The information you need to collect corresponds to options you'll need when you run .tsm configuration settsm
Most of the following tsm options are also used to configure Tableau Server deployments that operate behind a load balancer. For more information, see Add a Load Balancer.
| Item | Description | Corresponding optiontsm configuration set |
|---|---|---|
IP address or CNAME | You can either enter an IP address or a CNAME for this option. The public IP address or addresses of the proxy server. The IP address must be in IPv4 format, such as , and it must be a static IP. If you are unable to provide a static IP, or if you are using cloud proxies or external load balancers, you can specify the CNAME (Canonical Name) DNS value that clients will use to connect to Tableau Server. This CNAME value must be configured on your reverse proxy solution to communicate with Tableau Server. | gateway.trusted |
| FQDN | The fully qualified domain name that people use to reach Tableau Server, such as . Tableau Server doesn't support context switching for this option. For example, the following URL is not supported: .tableau.example.comexample.com/tableau | gateway.public.host |
| Non-FQDN | Any subdomain names for the proxy server. In the example of , the subdomain name is .tableau.example.comtableau | gateway.trusted_hosts |
| Aliases | Any public alternative names for the proxy server. In most cases, aliases are designated using CNAME values. An example would be a proxy server and CNAME entries of and .bigbox.example.comftp.example.comwww.example.com | gateway.trusted_hosts |
| Ports | Port numbers for traffic from the client to the reverse proxy server. |
|
If you are using a distributed installation of Tableau Server, then run the following commands on the initial node in your cluster.tsm
Enter the following command to set the FQDN that clients will use to reach Tableau Server through the proxy server, where is the FQDN:
nametsm configuration set -k gateway.public.host -v "name"例如,如果通过在浏览器中输入来访问 Tableau Server,请输入以下命令:
https://tableau.example.comtsm configuration set -k gateway.public.host -v "tableau.example.com"输入以下命令以设置代理服务器的地址或 CNAME,其中 IPv4 地址或 CNAME 值:
server_addresstsm configuration set -k gateway.trusted -v "server_ip_address"如果您的组织使用多个代理服务器,请输入多个 IPv4 地址 ,用逗号分隔。不支持 IP 范围。要改进 Tableau Server 的启动和初始化,请尽量减少 的条目数。
gateway.trusted输入以下命令以指定代理服务器的备用名称,例如其完全限定的域名、任何非完全限定的域名和任何别名。如果有多个名称,请用逗号分隔这些名称。
tsm configuration set -k gateway.trusted_hosts -v "name1, name2, name3"例如:
tsm configuration set -k gateway.trusted_hosts -v "proxy1.example.com, proxy1, ftp.example.com, www.example.com"如果代理服务器使用 SSL 与互联网通信,请运行以下命令,该命令会告知 Tableau 反向代理服务器使用的是端口 443 而不是端口 80:
tsm configuration set -k gateway.public.port -v 443注意:如果代理服务器使用 SSL 与 Tableau Server 通信,则必须在 Tableau Server 上配置并启用 SSL。
输入以下命令以提交配置更改:
tsm pending-changes apply如果挂起的更改需要重新启动服务器,则该命令将显示一个提示,让您知道将重新启动。即使服务器已停止,也会显示此提示,但在这种情况下,不会重新启动。您可以使用该选项禁止显示提示,但这不会更改重新启动行为。如果更改不需要重新启动,则会在不提示的情况下应用更改。有关详细信息,请参阅应用 tsm 挂起更改。
pending-changes apply--ignore-prompt
配置反向代理服务器以使用 Tableau Server
当客户端通过反向代理访问 Tableau Server 时,必须保留(或添加)特定的邮件头。具体来说,消息链中的所有代理服务器都必须在 和 设置中表示。gateway.trustedgateway.trusted_hosts
下图显示了代理服务器直接与 Tableau Server 通信的单跃点消息链的示例标头:

下图显示了多跃点消息链的示例标头,其中消息在连接到 Tableau Server 之前将遍历两个代理服务器:

下表描述了这些标头是什么,以及它们与 Tableau Server 上的配置设置有何关系:
| 头 | 描述 | 相关 Tableau 服务器设置 |
REMOTE_ADDR和X-FORWARDED-FOR (XFF) | Tableau Server 需要这些标头来确定请求的来源 IP 地址。 标头必须按照连接发生的顺序向 Tableau Server 提供 IP 地址链。X-FORWARDED-FOR | 您设置的 IP 地址必须与 中提供的 IP 匹配。如果向 中发送了多个地址,则其中一个地址必须与 中提供的 IP 匹配。gateway.trustedREMOTE_ADDRgateway.trustedREMOTE_ADDR |
HOST和X-FORWARDED HOST (XFH) | 这些标头用于在 Tableau Server 答复客户端时生成指向它的绝对链接。 标头必须按照连接发生的顺序向 Tableau Server 提供主机名。X-FORWARDED-HOST | 标头中显示的主机名必须包含在 中指定的主机名中。X-FORWARDED-HOSTgateway.trusted_hosts |
X-FORWARDED-PROTO (XFP) | 如果为从客户端到代理的流量启用了 SSL,但对于从代理到 Tableau Server 的流量未启用 SSL,则需要此标头。 对于未沿消息路由的每个跃点维护 HTTP 或 HTTPS 的方案,标头非常重要。例如,如果反向代理需要外部请求使用 SSL,但反向代理与 Tableau Server 之间的流量未配置为使用 SSL,则需要标头。某些代理解决方案会自动添加标头,而其他代理解决方案则不会。最后,根据您的代理解决方案,您可能必须配置端口转发以将请求从端口 443 转换为端口 80。 相关知识库文章:升级后 SAML 出现“无法登录”和“用户名或密码无效”错误. | 反向代理上的端口配置(来自客户端的入站连接和到 Tableau Server 的出站连接)必须在相应的参数中指定:,这是客户端用于连接到代理的端口。 如果代理服务器使用 SSL 与 Tableau Server 通信,则必须在 Tableau Server 上配置并启用 SSL。 |
验证反向代理设置
要验证反向代理设置,请使用 Tableau Server Web 制作或 Tableau Desktop 发布工作簿和数据源。如果您使用 Web 浏览器从互联网连接到 Tableau Server,请验证您是否正在使用推荐的浏览器.发布和查看使用现有数据源的工作簿以及已发布的数据源。使用以下链接熟悉以最终用户身份与 Tableau Server 的连接。
| 任务 | 文档 |
|---|---|
| Web 制作概述。 | 在 Web 上使用 Tableau |
| 从 Tableau Desktop 或 Web 浏览器登录到 Tableau Server。 | 登录到 Tableau 服务器或联机 |
| 将工作簿发布到 Tableau 服务器。 | 发布工作簿 |
| 发布数据源。 | 发布数据源 |
| 从 Tableau Server 打开工作簿。 | 从服务器打开工作簿 |
| 注销服务器(带桌面)。 | 登录到 Tableau 服务器或联机 |
| 从 Web 浏览器下载工作簿。 | 下载工作簿 |
| 检查以确保 tabcmd(来自非服务器客户端)正常工作。 | 标签 |





